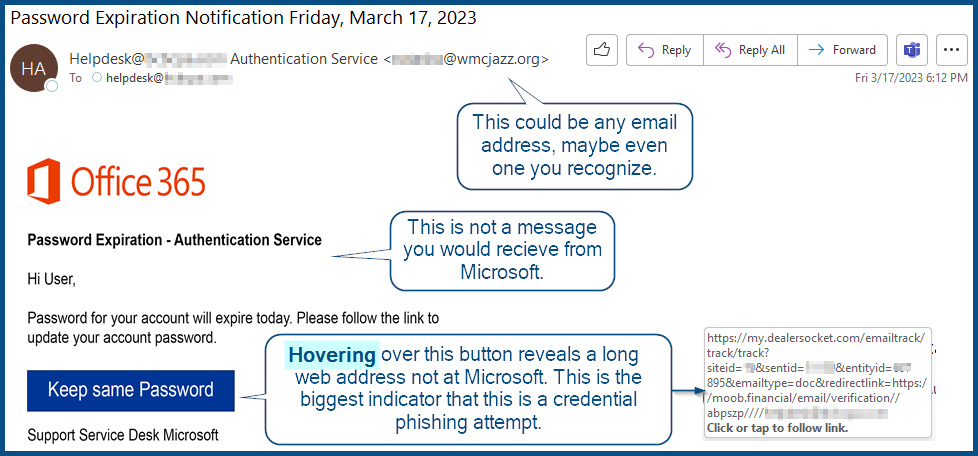
LastPass the popular password manager, has suffered yet another major breach. This has put customers’ online passwords at risk and endangered their data.
In late December, LastPass CEO Karim Toubba acknowledged in a blog post that a security incident the company disclosed in August eventually led to an unauthorized party stealing customer account information and sensitive vault data. The breach is the latest in a lengthy and troubling string of security incidents involving LastPass that date back to 2011.
An unauthorized party was able to gain access to unencrypted subscriber account information like LastPass usernames, company names, billing addresses, email addresses, phone numbers and IP addresses, according to Toubba. That same unauthorized party was also able to steal a copy of customer vault data
If you were a “LastPass” subscriber, what should you do?
LastPass estimates it would take “millions of years” to guess your master password — if you’ve followed its best practices. If you used a complex master password that was only used for LastPass, your LastPass vault is fairly safe.
The vault is encrypted, and your master was not stored at LastPass, so the thieves did not get a copy of your master password.
The problem is that the threat actor has two strategies to guess your master password. The quickest and easiest method is to search password databases from other data breaches for your LastPass account name and then try every combination they have. This is known as Credential Stuffing. It would take only seconds to try the combinations. The threat actor will even search for minor variations like adding numbers to the end of the password or changing the one special character at the end of the password. If you don’t re-use passwords, credential stuffing doesn’t work.
The second method is a brute force attack that uses a trial-and-error approach to systematically guess login info, credentials, and encryption keys. The cyber-attacker submits combinations of usernames and passwords until they finally guess correctly. If you used the LastPass recommended complexity combined with their encryption, brute force would take too long to be useful. If you didn’t use a long complex password, or your master password has been leaked through re-use, your password might be guessed in something between minutes and millions of years.
The safe approach is to operate under the assumption that your user and vault data are in the hands of an unauthorized party with ill intentions, and they are working at trying to unlock your vault.
If you haven’t — or if you just want total peace of mind — you’ll need to spend some serious time and effort changing your individual passwords. You might want to transition away from LastPass while you update your passwords.
With that in mind, here’s what you need to do immediately if you’re a LastPass subscriber:
- 1. Find a new password manager. Given LastPass’ history with security incidents and considering the severity of this latest breach, now is a great time to seek an alternative.
- 2. Change your most important passwords immediately. This includes passwords for anything like online banking, financial records, internal company logins and medical information.
Don’t forget the email account that you use for resetting your forgotten passwords is one of those ‘important passwords’
Make sure these new passwords are strong and unique.
- 3. Enable two-factor authentication wherever possible. While you are changing your passwords, make sure to enable two factor authentication on any online account that offers it. This will give you an added layer of protection by alerting you and requiring you to authorize each login attempt. That means even if someone ends up obtaining your new password, they shouldn’t be able to gain access to a given site without your secondary authenticating device (typically your phone). We will be posting an article soon about multi-factor authentication.
- 4. Change every single one of your other online passwords. It’s a good idea to change your passwords in order of importance here too. Start with changing the passwords to accounts like email and social media profiles, then you can start moving backward to other accounts that may not be as critical.
- 5. Change your master password If you choose to stay with LastPass. This doesn’t change the threat level to the stolen vaults, it will still help mitigate the threats of any potential future attack.
If you find that your data has been breached or you are experiencing unusual functionality with your business computer systems, contact your IT Department. If you are a business owner, Cogent Technology Solutions can assist in remediating a Cyber Attack. Contact us immediately at http://www.cogent-ts.com/get-started/