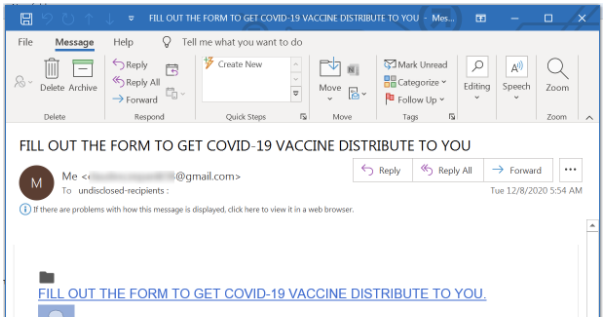
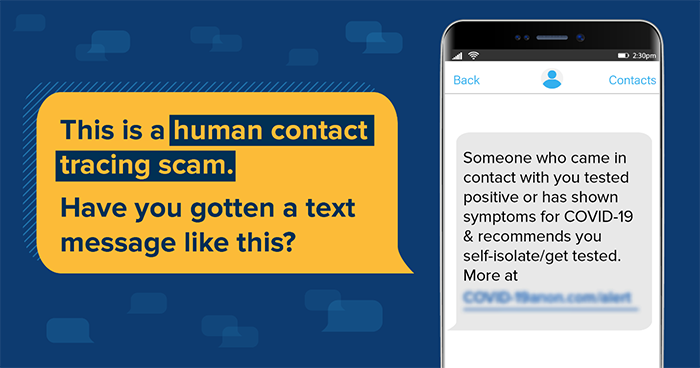
Passwords have become an essential part of our daily lives. We use passwords for everything from social media accounts to online banking. With your banking and medical information available online, the need for secure passwords is more important than ever.
Here are our top 5 password practices.
- Use a unique password for each account. This way, if one of your passwords leaked in a data breach, it will not affect your other accounts. Don’t cheat, the bad guys know all about substituting a 3 for B and adding numbers or special symbols at the end.
If your “ILoveSummer!” password is leaked, any variation can be tried in fractions of a second. In no time, the identity thief will find that you used “!lov3summer2” for your bank account password. - Enable multi-factor authentication (MFA) whenever possible. MFA adds an extra layer of security by requiring you to enter a code or use another device to verify your identity when logging in to an account. At a minimum, your primary email account, banking, financial, health care and password manager accounts should require MFA.
- Make your passwords long and complex. Use at least 12 characters and include a mix of uppercase and lowercase letters, numbers, symbols, and spaces. Consider using a passphrase where possible if you don’t use a password manager. A passphrase is a very long (over 20 characters) list of words that resemble a sentence. Passphrases are much easier to remember than 15 random characters.
Avoid using common words, phrases or quotes that can be easily guessed or cracked by hackers when creating your passphrase. - To make long complex passwords easier to deal with, use a password manager. A password manager will save and encrypt your passwords in a vault that only you can access (and is protected with MFA.) Password managers also help you create strong and random passwords for each account and warn you of re-use.
- Don’t use personally identifiable information (PII) in your passwords. This includes your name, date of birth, address, phone number, email address or any other information that can be linked to you.
Bonus Tips
- Change your passwords only when necessary. Changing your passwords too frequently can make them harder to remember and more likely to be reused or written down. A good rule of thumb is to change your passwords only when you suspect a breach or when prompted by a legitimate service provider.
- Don’t share your passwords with anyone else. Not even with friends or family members who may have good intentions but may compromise your security unintentionally.
- Don’t send your passwords by email, instant message or any other means of communication that are not securely encrypted. Hackers can intercept these messages and steal your passwords easily.
- Avoid using public computers or networks to access your accounts online unless absolutely necessary as they may have malware installed that can capture keystrokes.
Following password best practices will help keep your online accounts safe and secure. By using strong passwords, avoiding common mistakes, and being cautious of cyber threats, you can significantly reduce the risk of your accounts being compromised. Remember to enable two-factor authentication wherever possible for your important accounts.